What is CyberGate:
CyberGate is a powerful, fully configurable and stable Remote Administration Tool coded in Delphi that is continuously getting developed. Using cybergate you can log the victim's passwords and can also get the screen shots of his computer's screen. You can connect o multiple victims in single time. One should no know what is the ip-address of the victims' computers. That is the main benefit. What you have to do is to spread the server file to the vicitms or the people whom you want to infect. Also there is a file manager utility using which you can explore the data of the victim. So, its much exciting, therefore i thought to give a tutorial about it, since it can also be used for constructive purpose i-e you can view the clients of you office or your homies, that what are they doing at computer. Rather they are sincere or not. I am going to show you step by step guide, by creating my own server. I created Hackersthirst to produce awareness among people about general tools usage also.Steps For creating a successful cybergate server:-
Step 1) I have hosted to cybergate for dowloading to the two locations, as often i get messages that download link is not working.Download CyberGate:
First Download Location of Cyber Gate
Second Downalod Location of Cyber Gate
Step 2) Now, It will be better that you temporarily disable your antivirus software. and also other security software if its the case that CyberGate isn't working for you.
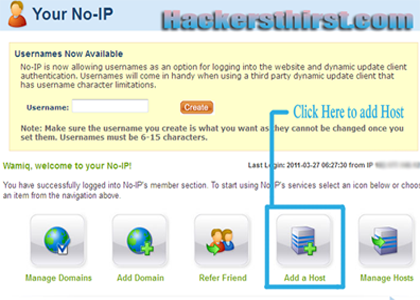
Step 3) Set up your account at no-ip.com , If you are already registered that just login. After loging in add a host. Picture Demonstration is given below, since in last post of pro-rat people asked lots of question.
After this, Type your email id here, Like i did:
Now, Fill the forum provided with your real preferences or fake :P , Do what you like. After that you will receive a confirmation email in your inbox, Like the one you receive while subscribing to Hackersthirst, Click the confirmation link provided there, and thus you will have an activated and verified account. Login there. Now, What you have to do, is given below in step 4 with pictures!
Step 4) You have to add host, Like this, after getting logged in!
After that, fill like this, Replace hackersthirst with your desired name!
Thats it you are done, with following info:
Host name: hackersthirst.zapto.org
Host Type: DNS Host (A) , Further leave other fields blank like i did.
Host process is now finished now i am moving to no-ip client.
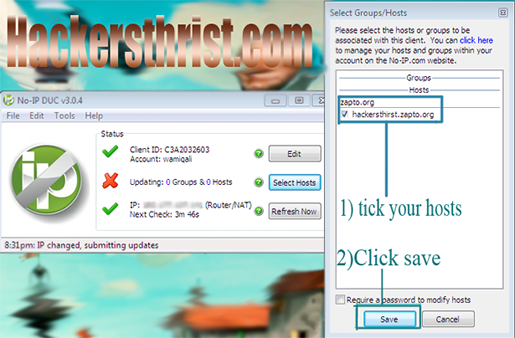
Step 5) Download no-ip client from here. Download according to your OS, It supports windows, mac or linux. After downloading install the program, And then run it, You will promted to put in your email id along with password which you used to login to the no-ip.com, After loging in, Do what i did in the following screen shot!
Note: Always keep this software opened, Whenever cyper gate is running.Thats it, We have done with no-ip.com, Now procees forward with cybergate!
Step 6) Extract The Cybergate archive You Downloaded In The Beginning To Your Desktop! Once Extracted, Open It & Wait 20 Seconds For The Agreement To Pass! When It's Open, Press: Control Center -> Start.
and then press, Control Center -> Options -> Select Listening Ports, After this a popup will appear fill that like this:
Explaining further:
At first, Write "100" In That Little Box And Press The Blue Arrow. Then It Should Appear Under "Active Ports"
Active Ports: The Port You Will Forward Later using modem or uTorrent!
Connections Limit: The Max Amount Of Victims You Can Have.
Connection PW: The Connection Password. Use "123456"
[V] Show Password: (Shows Password)
Once This Is Done, Press "Save"!
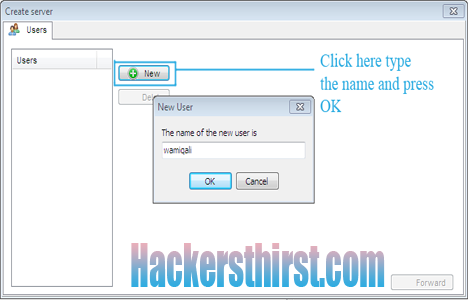
Step 7) After this we are going to create the server, Go to, Control Centre -> Build -> Create Server
After adding name, select the name i-e wamiqali and Press forward.Now, Following windows will appear, Fill it like this:
Now, Click ok, It will be added in the list, After that select 127.0.0.1 and click delete. So, that following form will come in front of you:
Note: If You Want To Try The Server On Yourself, Then Delete Both:Step 8) After this move on to the installer tab, and do what i did in the following screen shot:
- 127.0.0.1:999
- hackersthirst.zapto.org
And Replace Them With; 127.0.0.1:100 Since 127.0.0.1 Means "Local Computer & LAN Internet"
Well, i think for this section no further explanation is required, things themselves in the screen shot are telling that what they are meant to do.
Step 9) Now move on to the Anti-Debug tab, and follow guideline as shown in the screen shot:
Step 10) Move on to the final tab, that is Create Server. and do what i did!
So, You are done!
Step 11) (There are many ways for this step, You can also google for some other better way) Now you have to port forward, For this purpose, login to your router or modem (Recommended way) and forward the port which you have used while making the cber gate i-e 100, But another quick tweak is this that simply run uTorrent and select Options > Preferences > Connection than enter there in Listening Ports, the value of port you want to be forwarded (e-g 100) than select Apply.After that Exit the uTorrent from the tray of the windows. and go to http://canyouseeme.org/ and check whether port is access-able or not. If its access-able, You will get this message for port 100:
Success: I can see your service on 100.100.200.200 on port (100)
Your ISP is not blocking port 100
What to do if RAT is not Connecting?
Make Sure That....
1) You are properly port-forwarded if using a router.
2) You have the No-IP Client installed and running.
3) Your DNS entries are correctly spelled when building your server.
4) The password in Listening Ports and the password your server uses are identical.
5) You are Listening on the correct ports.
6) Your Firewall is letting connections through on the port you're listening on.
7) Your server is added to excluded files in your Antivirus and Firewall.
Once You've Port Forwarded Your Port: "100" Then Just Get It Crypted And Start Spreading. After that you will surely get some victims But i will surely point out here that don't use this for bad purpose!

















0 komentar:
Posting Komentar